15+ Fakten über Icmp Flood Ip? Such an attack works by overwhelming the victim device with icmp request (ping) commands over the network, making it impossible for the victim to send icmp responses in time.
Icmp Flood Ip | The ip of the attacker and the victim I have received numerous dos icmp flood attacks through my c6300 cable modem each day that cause either slowness or cause my router to restart. An attacker sends udp packets with a spoofed ip sender address to random ports on the target system. In this case the victim server is flooded with fabricated icmp packets from a wide range of ip addresses. It is common for generating packets but mostly used for denial of service attacks or flooding.
Packet flood generator as the name stands is a projet to produce a threaded traffic generator program, it has support for generating ip, tcp , udp, icmp and igmp packets, also has as feature to keep the connection up. In icmp flood attacks, the attacker overwhelms the targeted resource with icmp echo request (ping) packets, large icmp packets, and other icmp types to significantly saturate and slow down the victim's network infrastructure. Dos icmp flood on c6300. The internet control message protocol (icmp), which is utilized in a ping flood attack, is an internet layer protocol used by network devices to communicate. An icmp flood ddos attack requires that the attacker knows the ip address of the target.
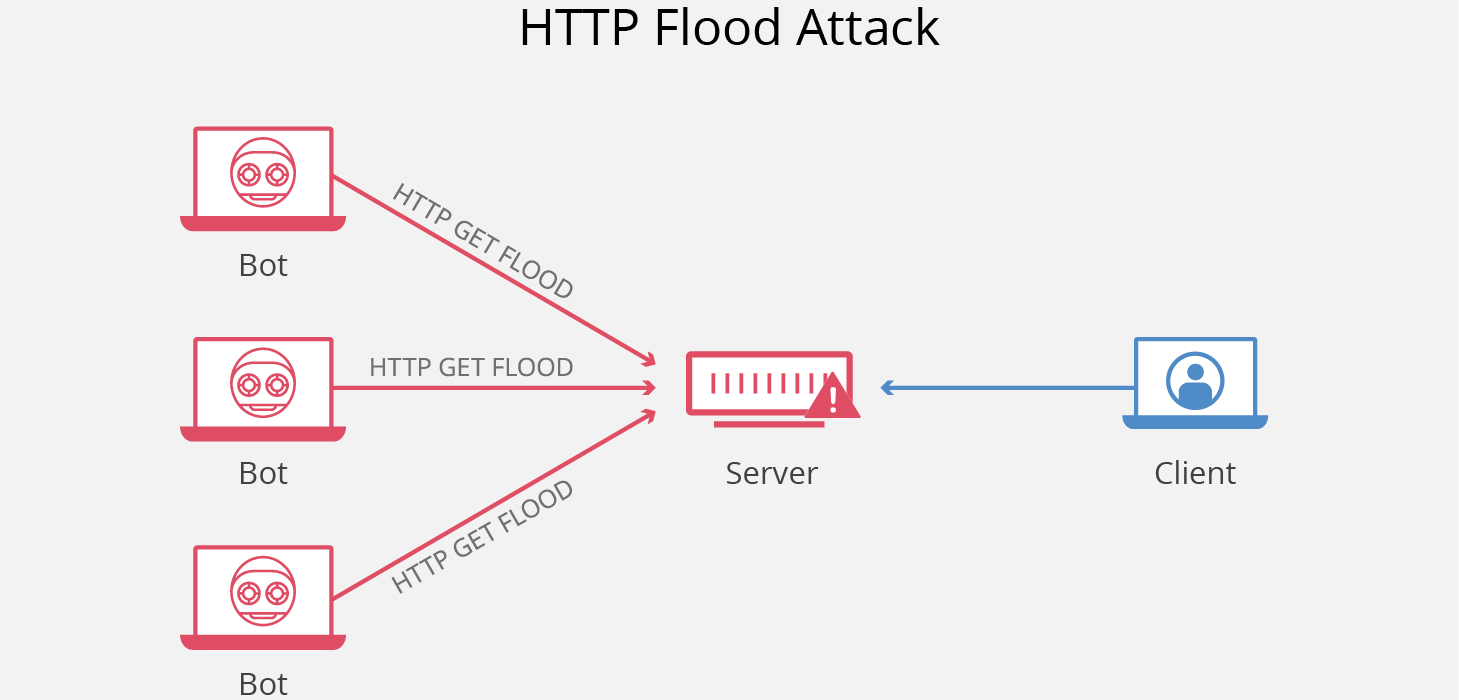
In this case the victim server is flooded with fabricated icmp packets from a wide range of ip addresses. Red is more efficient than syn cookies and can handles larger attacks, but doesn't discern between good and bad traffic. In icmp flood attacks, the attacker overwhelms the targeted resource with icmp echo request (ping) packets, large icmp packets, and other icmp types to significantly saturate and slow down the victim's network infrastructure. Usually icmp packets are sent without any payload to each specified protocol on the target machine. A broadcast storm of pings overwhelms the target system so it can't respond to legitimate traffic. Icmp error messages (protocol/port unreachable) can be used to find out the open ports to an ip address or a lan segment. Packet flood generator as the name stands is a projet to produce a threaded traffic generator program, it has support for generating ip, tcp , udp, icmp and igmp packets, also has as feature to keep the connection up. I have received numerous dos icmp flood attacks through my c6300 cable modem each day that cause either slowness or cause my router to restart. Since udp is a connectionless protocol, the server uses the internet control message protocol (icmp) to inform the sender that the packet could not be delivered. In terms of the technology, the ping flood is based on the internet control message protocol (icmp). The threshold must be set carefully as too small a threshold may affect unintented traffic and too large a threshold may not effectively protect from an attack. Icmp flood attack threshold (icmp packets / sec) the rate of icmp packets per second sent to a host, range or subnet that triggers icmp flood protection. The malefactor aims to fill the channel and overload the victim server with fake requests.
To mitigate and prevent an icmp flood #ddos #attack: 7 this week last update: Ip fragmentation attacks are a common form of denial of service attack, in which the perpetrator overbears a network by exploiting datagram fragmentation mechanisms. The malefactor aims to fill the channel and overload the victim server with fake requests. Icmp error messages (protocol/port unreachable) can be used to find out the open ports to an ip address or a lan segment.
A ping flood or a distributed denial of service (ddos) attack is a form of attack in which someone sends a lot of ping requests to a host and the host becomes almost inaccessible to the routine traffic. The network diagnostic tools traceroute and ping both operate using icmp. Internet control message protocol flood icmp is a flooding attack. Since udp is a connectionless protocol, the server uses the internet control message protocol (icmp) to inform the sender that the packet could not be delivered. A good example of this is a worm attack, such as an attack by the sql slammer worm. The malefactor aims to fill the channel and overload the victim server with fake requests. Unlike in tcp, icmp packets do not require confirmation of receipt therefore detecting junk traffic in icmp is as difficult as in. Ping flood, also known as icmp flood, is a common denial of service (dos) attack in which an attacker takes down a victim's computer by overwhelming it with icmp echo requests, also known as pings. Different types of scanners are available in the market that use icmp to check whether a port is open or not. In the event of a udp flood attack, the following process occurs: The ip of the attacker and the victim The ip of the attacker and the victim as shown in image 2 the packet is an icmp type 3 packet (time exceeded). Internet control message protocol (icmp) is a connectionless protocol used for ip operations, diagnostics, and errors.
To avoid this kind of situation, network administrators usually block icmp on their network. An attacker sends udp packets with a spoofed ip sender address to random ports on the target system. In this case the victim server is flooded with fabricated icmp packets from a wide range of ip addresses. A ping flood involves flooding a target computer with icmp echo request packets. In icmp flood attacks, the attacker overwhelms the targeted resource with icmp echo request (ping) packets, large icmp packets, and other icmp types to significantly saturate and slow down the victim's network infrastructure.
Understanding the attack starts with understanding the process of ip fragmentation, a communication procedure in which ip datagrams are broken down into small packets, transmitted across a. The internet control message protocol (icmp), which is utilized in a ping flood attack, is an internet layer protocol used by network devices to communicate. Preventing an #icmp flood ddos attack can be accomplished by disabling the icmp functionality of the targeted router, computer or other device. Unlike in tcp, icmp packets do not require confirmation of receipt therefore detecting junk traffic in icmp is as difficult as in. Icmp rate limiting many attacks create a dos attack by sending a flood of traffic to a device or devices that do not exist, causing an intervening router to reply back with an icmp unreachable message for each unknown destination. The ip of the attacker and the victim as shown in image 2 the packet is an icmp type 3 packet (time exceeded). Icmp flood, icmpv6 flood, and. Internet control message protocol flood icmp is a flooding attack. Dos icmp flood on c6300. To mitigate and prevent an icmp flood #ddos #attack: The malefactor aims to fill the channel and overload the victim server with fake requests. The network diagnostic tools traceroute and ping both operate using icmp. An icmp flood ddos attack requires that the attacker knows the ip address of the target.
Icmp Flood Ip: As seen in the image 1 an icmp flood of type 8 consists of a high volume of icmp echo packets.

Posting Komentar
Posting Komentar